I’ve used a lot of different software in a tireless effort to brute force a password out of a single PDF. So far, Elcomsoft Distributed Password Recovery certainly helps to speed up the process dramatically, but is it enough to reasonably crack a standard 8 character password in a reasonable amount of time?
As it turns out, that depends on what type of file you are trying to recover the password on. For example, PDF files are unable to take advantage of GPU acceleration (such as NVIDIA’s CUDA), while WPA/WPA2 (.cap/.wph files) are supported. Either way, be prepared to wait a long time, or drop a lot of money on a lot of CPU/GPU power because once you get up to just a measily 8 characters, it can take years.
Brute forcing passwords is awful. It takes a really long time, even for the simplest of passwords. I started off using Elcomsoft’s Advanced PDF Password Recovery. Tried their dictionary attack, when that failed I then tried their brute force attack which averaged ~17,000 passwords per second on my old work system, an Athlon X2 4600+ (circa 2006). Of course, using “all printable” characters including spaces and special symbols, upper and lowercase letters and numbers promptly gave me an ETA of “more than one year” after it reached six characters. That’s when I began trying the distributed recovery.
Using normal household CPUs, it’s pretty hopeless. See for yourself, in the photo below, I’ve got 11 systems (23 CPU cores total) at 161,018 passwords/sec.
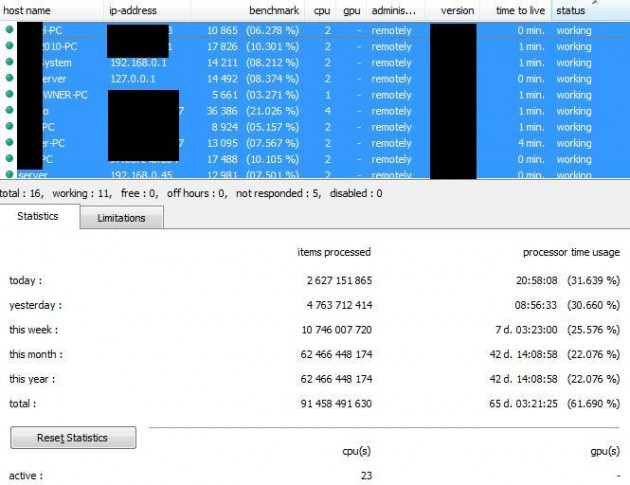
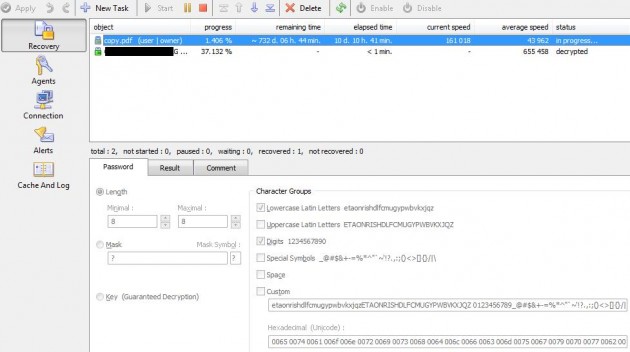
On the “Recovery” tab (shown below), you’ll notice a few things. The “average speed” is how the remaining time is calculated. In this case, 43,962 passwords/sec, and at that rate it would take 732 days to complete a full brute-force using only lowercase letters and numbers. Since the current rate is 161,018 passwords/sec. it’d be completed about 3 times earlier, but that’s still a really long time!
Another thing you may have noticed on the Recovery tab is that it only really supports two methods of recovery. Brute, and key. Key decryption naturally only works for 40-bit keys since it will essentially try every possible key for that space and guarantee a recovery. I would imagine that you are very unlikely to encounter an outdated encryption method such as this. As for brute, well, there’s very little control. You can only choose between so many options, and there’s no ability to load in a custom dictionary or perform a hybrid dictionary/brute attack. The “mask” feature is only useful if you know a part of the password, and let’s face it, you don’t.
So, you’re stuck with a very crude set of brute force “options” and without a huge number of PCs in your swarm (hundreds? thousands?), it’s going to take centuries. That brings me to another thing, this software is seriously expensive. The smallest package is $599 for 20 clients. And, as I’ve demonstrated, that’s definitely not going to be enough. The next tier up is $1,199 for 100 clients, which would seem more likely to actually recover a password in a more reasonable amount of time, I suppose…
ESDPR will work with a clusters of Tableau TAC1441s, but, as you’ll see, that’s gonna cost you quite a bit of money to get any serious performance out of your recovery.
In order to get any real performance or results from this product, I’ve concluded you need far too much money to be worth the effort. In addition, there’s several features missing from software this expensive. For example, what if I want to have 10 computers working on a PDF while I reserve the other 10 computers (that possibly have GPUs) to perform an attack on a different filetype such as an Excel 2007 file? You can’t. You have to wait until one file has finished before the next will begin. So, mark your calendar for 2039.
The calculations take a really long time, so, what if you need to change the hostname on your distributed agents remotely? You can’t. You have to go to each agent computer manually and change it, and if you have hundreds of systems…
Other issues are an ongoing concern as well, as an example, sometimes pushing “disable” on an agent won’t stop the calculations. The agent will keep running the math even with the “disable” button set for a long time. I’ve found that setting an agent’s “limitations” to “off hours” to be more reliable to stop the calculations than to attempt to use the “disabled” button. Of course, these kinds of issues can be fixed with updates, but nevertheless I still don’t really have a clue as to how good of a job the server is doing at managing which agent is handling what passwords attempts.
If this software had some advanced custom & hybrid brute/dictionary attack methods, it would carry far greater value. Unfortunately, as it presently stands, it’s just too limited and far too expensive to be of any use to anyone.
admin@variableghz.com

I know this post is old but i just wanted to add. We are using it atm to recover a password from lotus notes, its only rc2 64 bit and its estimating half a million days :( and we are running it on HP Blade workstations with 24 cores a peice and 96gbs of ram, we have 1 and a half enclosures working on it. it was a little disappointing
I purchase this product thinking it could do the job of recovery files that password were not remembered. Well guess what did not work and even support could not help me so I asked for a refund and guess again big dissapointment they cannot give it as there product works but not for strong password, I guess stupid password it works but too complicated ones it does not work do not waste your time or money with this product